The information provided on this page represents part of our official data protection and security policies. For additional information, please visit our description of rights and duties.
We are a service consultancy and training organization. We provide information and service both on line and face to face.
No.
Sensitive personal data, such as your race, your religion, your medical characteristics, or your political beliefs, are not recorded.
The exact personal data recorded depends on the type of service used or the type of contact made. Please see the matrix below for the details.
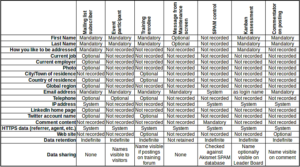
Mandatory: User must enter these data
Optional: User may enter these data, or they may be added from external sources
System: The system automatically records these data
Not recorded: These data are not recorded or are completely ignored
The personal data comes from three sources:
- the data that you, yourself, provide
- the data that is automatically recorded by the information system (such as IP addresses)
- the data about your visits to our site, such as what pages you visit, how long you stay there, from which pages you are coming to which pages you are going; and how you interact with a page, such as whether you purchase a service from us or not
- the data about you that is available on public sources or from sources where you have already given permission to make the data visible.
The principal sources of data are LinkedIn and Twitter. The data visible there is under the control of the user.
We use your personal data to send you information to which you have subscribed and additional information about our services. We may use that data to segment our communications, such as by language or by geographical region, to avoid sending you irrelevant communications. We use your credentials for controlling access to our services. We may ask you for further information about our services to adapt them to your needs. If we find that our services are being used in a way that does not conform to our policies, we may use personal data in an attempt to identify the perpetrators of that misuse and correct any dysfunctions.
Your interactions with our sites may trigger other communications to you, such as a reminder that you have left a service in a shopping cart.
Send a request by email to the email address in the footer of this page. We may ask for further information to ensure your identity.
Send a request by email to the email address in the footer of this page. You may be asked for further proof of your identity.
Any personal data that you have entered yourself, such as when subscribing to our mailing list, you may modify yourself at any time. A link for making changes is provided in the footer of every email sent via this mailing list. You may be asked to provide additional information to ensure your identity.
You may request that other data be changed by sending your request to the email address in the footer of this page.
Your personal data is used in various ways:
- As connection credentials to our web sites
- To send you messages, if you have subscribed to our mailing list
- To submit payment information to a third party service, such as PayPal or Stripe, in case you purchase a service
- To segment the subscribers on the mailing list to avoid sending you inappropriate messages, such as segmentation by preferred language or by country of residence
- To offer you benefits, such as discounts on services, based on your interactions with our services
- To optimize our way of presenting information, such as via A/B tests or counts of visits to our web site pages.
Your personal data may be visible to the following third parties:
- Payment gateways (PayPal or Stripe)
- Mailing providers (MailChimp)
- Web tracking services (Google)
- Web site hosting (Infomaniak)
Please refer to their respective sites for additional information on how they handle personal data.
We do not share any personal data with any other third parties.
If, however, at some time in the future we plan to share your data in this way, it will only be following your explicit permission to do so.
In addition to sensitive personal data, we do not store any financial information, such as credit card numbers. We neither seek nor collect nor store any government identification numbers. We make no attempt to identify site visitors based on such data as the browser or client used to connect with our web sites. Thus, while the IP addresses of connections to our web sites are logged, we make no attempt to correlate those addresses with any persons. They remain anonymous.
Access to your personal information is limited to our personnel and to whoever controls the email address under which you are identified. You are responsible for controlling access to that email address.
Note that this web site is excluded from the Google FLoC system.
If we have any reason to believe that a third party is attempting to use your email address without your consent, we may ask for additional information to help confirm you identity.
In technical terms, access to our web site and to our mailing list is controlled by two factor authentication. All communications to our web site and our third party services are made using https. Access to our web site is controlled using an application firewall and state of the art web server security modules. Data is backed up regularly and stored using the same controls as the production data.
We choose our partners with whom your personal information might be shared based on their reputations for compliance with regulatory requirements and their approach to maintaining the security of the information to which they have access. Beyond the diligence with which we select partners, we do not take responsibility for any failures that might occur
