In another article, I spoke of vision management and risk management as the two pillars upon which organizations reside. As I have already spoken about vision, let’s take a minute to examine risk in the context of service management in a little more detail.
Risk management
Types of Tool Automation
Types of tool automation The fundamental difference between a software tool and most types of tools is that software can be programmed to automate one or more tasks. Most other tools do not automate work at all, only extending the capabilities of the wielder of the tool. Certain mechanical tools can automate a task, but, […]
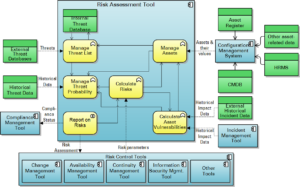
The Automation of Risk Assessment
Pre-industrial risk assessment Risk assessment remains a highly manual activity in all organizations I have ever seen. Some organizations have a structured approach to assessing, and then managing, risk. Others work largely with a seat of the pants approach. But in both cases, the activity of identifying risks and their magnitude and the creation and […]